In the world of phishing defense, email reputation is an incredibly valuable, but often overlooked, piece of intelligence.
While building Sublime, a detection and response platform for email security, we've encountered two principal phishing defense applications. First, for identifying email addresses created by threat actors to conduct malicious activity, and second, for identifying high reputation email accounts that have been compromised and are now being used for malicious activity. Both are non-trivial to solve.
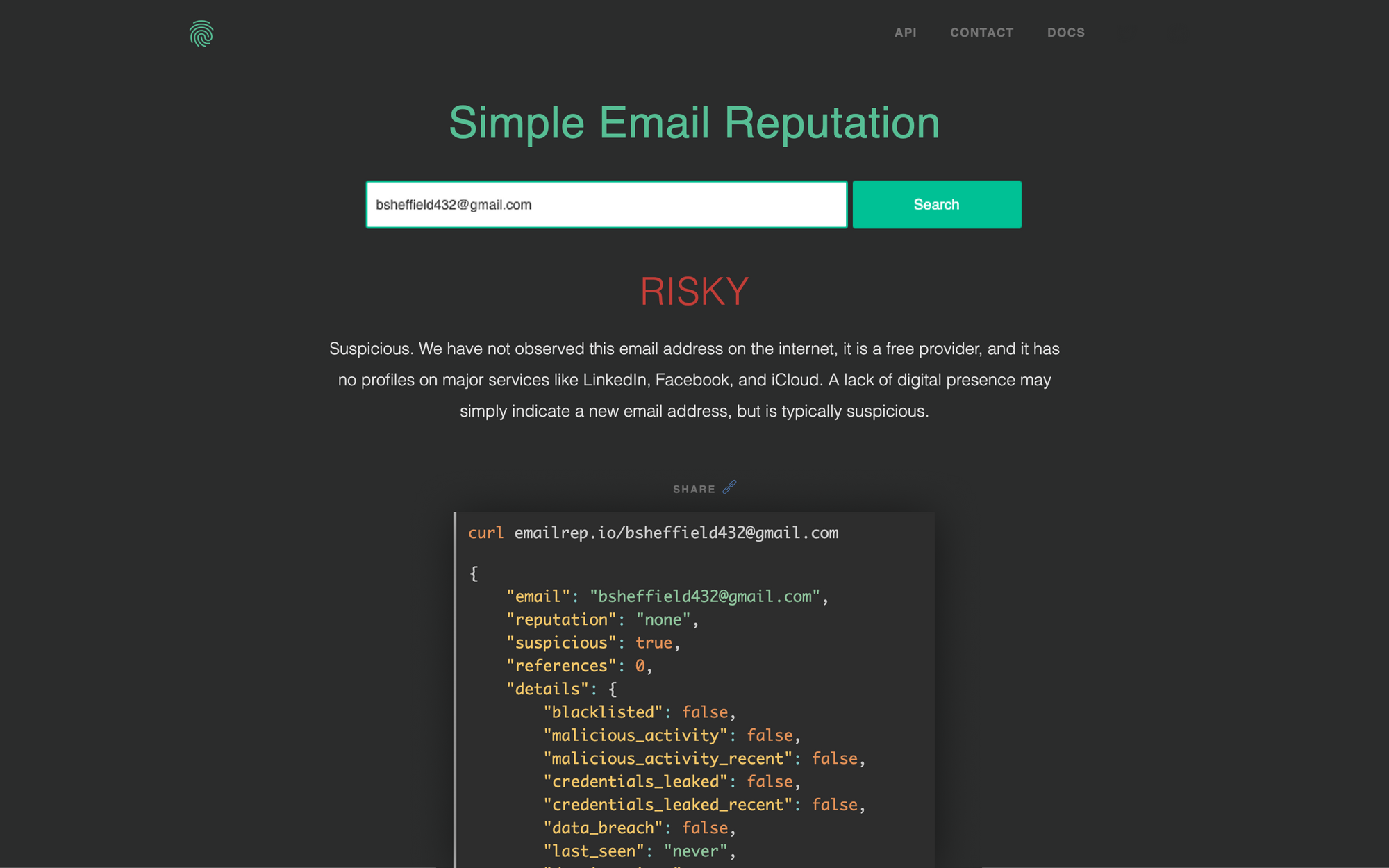
In the first case, these email addresses will often look indistinguishable from a legitimate sender. bsheffield432@gmail.com looks like a real person, but as we'll see later this email address has no reputation and is thus suspicious. In the latter case, these email addresses have many indicators of high reputation but are in fact temporarily malicious. Here we use what we call "temporal badness" to represent email addresses that are, for a time, suspicious.
EmailRep is a system of crawlers, scanners, and enrichment services that we built to solve these two problems. It uses inputs such as automated OSINT techniques, 3rd party services, and risk scoring to answer some key questions like:
- Is this email address deliverable?
- Has it already been blacklisted or otherwise seen doing naughty things like sending phishing emails, committing fraud, or spamming login forums?
- Has it been in a recent credential dump or leak, and is thus likely to be compromised?
- Has it been in historical data breaches, meaning it's likely to be a real email address (attackers aren't in data breaches because they haven't signed that address up for any services)
- If it's not a free provider, how old is the domain?
- What online presence does the address have on sites like LinkedIn, Facebook, and Twitter?
- Is SPF and DMARC enforced (i.e. is it spoofable)?
- and most fundamentally, is the email address "suspicious" or not. This is our proprietary synthesis of the above and many other factors.
The first case, a new address created for malicious activity, is illustrated well by bsheffield432@gmail.com. The curl command is dead simple:
curl emailrep.io/bsheffield432@gmail.com
And here's the response:
{
"email": "bsheffield432@gmail.com",
"reputation": "none",
"suspicious": true,
"references": 0,
"details": {
"blacklisted": false,
"malicious_activity": false,
"malicious_activity_recent": false,
"credentials_leaked": false,
"credentials_leaked_recent": false,
"data_breach": false,
"last_seen": "never",
"domain_exists": true,
"domain_reputation": "n/a",
"new_domain": false,
"days_since_domain_creation": 8748,
"suspicious_tld": false,
"spam": false,
"free_provider": true,
"disposable": false,
"deliverable": false,
"accept_all": false,
"valid_mx": true,
"spoofable": true,
"spf_strict": true,
"dmarc_enforced": false,
"profiles": []
}
}
In this case, bsheffield432@gmail.com is suspicious. If we append ?summary=true to our query, we also get a nice, human summary of why:
Suspicious. We have not observed this email address on the internet, it is a free provider, and it has no profiles on major services like LinkedIn, Facebook, and iCloud. A lack of digital presence may simply indicate a new email address, but is typically suspicious.
Since launching EmailRep in April this year, we've seen its use grow to hundreds of organizations, a number of which also use it for detecting fraudulent or malicious signups. And of course, we're using it every single day to spot sophisticated phishing attacks using throwaway or compromised accounts.
Reporting malicious senders
We've also been fortunate to have a number of security researchers and defenders sending us email addresses that they've spotted doing something malicious. Some of these are compromised accounts, and others are simply throwaways. To date, they've been sending us these via email and Twitter. Their efforts help make EmailRep better for everyone that uses it.
Today, we're excited to announce that verified individuals and organizations can now programmatically report malicious email addresses. Users can specify why they're reporting the email address and optionally expire the report if they believe it to be an account compromise.
Let's say we saw bsheffield432@gmail.com impersonating a co-worker and attempting to send us a malicious attachment. Here's the curl command:
curl -XPOST 'https://emailrep.io/report' -H 'key: [api_key]' -d '{"email": "bsheffield432@gmail.com", "tags": ["malicious", "bec", "maldoc"], "description": "Phishing email sent to accounting dept impersonating our CEO", "timestamp": 1562171178}'
And the available tags:
spam- Unsolicited spam or spammy behavior (e.g. forum submissions, unwanted bulk email)malicious- Malicious intent of any kind. Superset of the below tagscredential_phishing- Credential phishing, brand impersonationbec- Business email compromise, whaling, contact impersonation/display name spoofingbrand_impersonation- Impersonating a well-known brand (e.g. Paypal, Microsoft, Google, etc.)maldoc- Malicious documents, either directly (attachments) or indirectly (free file hosting sites)romance_scam- Romance scam, sextortionaccount_takeover- Legitimate email has been taken over by a malicious actorthreat_actor- Threat actor/owner of phishing kitbrowser_exploit- The hosted website serves an exploitgeneric_phishing- Generic phishing, should only be used if others don't apply or a more specific determination can't be made or would be too difficult
Full details, documentation, and multi-language code samples are all here. You can also check us out on Github.
EmailRep is just the first of many standalone services we'll release publicly as we continue to expand early access to Sublime itself. If you're interested in early access to Sublime or want to contribute, please say hi or check out sublimesecurity.com.